Identify your disk
sudo lsblk
Securely wipe your disk
Suppose we have found /dev/sdb
sudo dd if=/dev/zero of=/dev/sdb iflag=nocache oflag=direct bs=4096
The iflag=nocache (read) and oflag=direct (write) parameters are important because without them the dd command use data to/from RAM rather than the hard drive.
Create partition
Create a partition on the device
sudo fdisk /dev/sdb
Running lsblk again, we can see our new partition, /dev/sdb1.
Encrypt partition
# base
sudo cryptsetup luksFormat /dev/sdb1
# or check parameters
sudo cryptsetup -v -y -c aes-xts-plain64 -s 512 -h sha512 -i 5000 --use-random luksFormat /dev/sdb1
- -v
- verbose
- -y
- verify passphrase, ask twice and complain if they don’t match
- -c
- specify the cipher used
- -s
- specify the key size used
- -h
- specify the hash used
- -i
- number of milliseconds to spend passphrase processing (if using anything more than sha1, must be great than 1000)
- –use-random
- which random number generator to use
- –label
- set a label
- luksFormat
- to initialize the partition and set a passphrase
- /dev/sdb1
- the partition to encrypt
To see the configuration of the header, use the command below.
sudo cryptsetup luksDump /dev/sdb1
Backup the LUKS header
The LUKS header stores metadata about the LUKS device, as well as the master key, key files, etc…
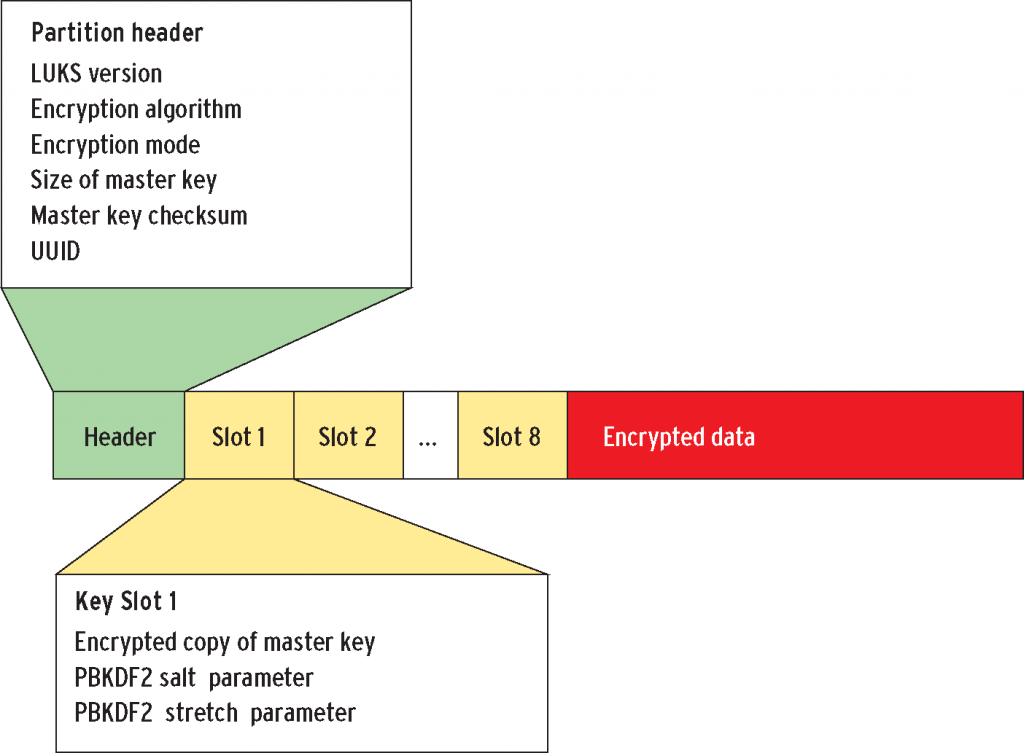
A LUKS format starts with the LUKS partition header and is followed by keys sectionand finally encrypted data. The header is where information about the used cipher, cipher mode, the key info, a uuid and a master key checksum is stored. After the key section the user data, encrypted by the master key, is stored. Slot Section contains 8 key-slot areas. The passphrases are used to decrypt a single master key. When a key slot is active, the key slot stores an encrypted copy of the master key in its key section. This encrypted copy is locked by a user password. The user can unlock the decryption for the key, which stores the master key. The master key the unlocks the bulk data. For a key slot, all parameters how to decrypt its key with a given password are stored in the header section.
| partion header (metadata) | key slots | data |
|---|---|---|
| cipher cipher mode the key info master checksum | SLOT 0-7 | ENCRYPTED DATA |
Add/Remove a Secondary backup key
# add
cryptsetup luksAddKey --key-slot 1 /dev/sdb1
# remove
cryptsetup luksRemoveKey --key-slot 1 /dev/sdb1
It’s best practice to backup the header as soon as you create the LUKS device, because if you damage the header all data will be lost.
Save header
sudo cryptsetup luksHeaderBackup --header-backup-file /path/to/file_backup.img /dev/sdb1
Restore header
sudo cryptsetup luksHeaderRestore --header-backup-file <file> <device>
Unlock the LUKS device
# volume01 is a name
sudo cryptsetup luksOpen /dev/sdb1 volume01
Create filesystem
sudo mkfs.ext4 /dev/mapper/volume01
Mount device
sudo mkdir -p /mnt/drive01
sudo mount /dev/mapper/volume01 /mnt/drive01
Unmount and close container
sudo umount /mnt/drive01
sudo cryptsetup luksClose /dev/mapper/volume01
Ways of mounting the encrypted drive
Manual Way
sudo cryptsetup luksOpen /dev/sdb1 volume01
sudo mount /dev/mapper/volume01 /mnt/drive01
# WORK AND THEN
sudo umount /mnt/drive01
sudo cryptsetup luksClose /dev/mapper/volume01
After OPEN you have to a regular filesystem